🝰 dusk is a deniable cloud drive
Installer User Guide FAQcurl -o- https://rundusk.org/install.sh | bashPaste the command above into your Terminal on macOS or Linux and press Enter to install.
 Trustless file storage, secure sharing, and programmable alerts.
Trustless file storage, secure sharing, and programmable alerts.
 No server to hack, database to seize, or company to subpoena.
No server to hack, database to seize, or company to subpoena.
 End-to-end privacy, anonymity, and censorship resistance.
End-to-end privacy, anonymity, and censorship resistance.
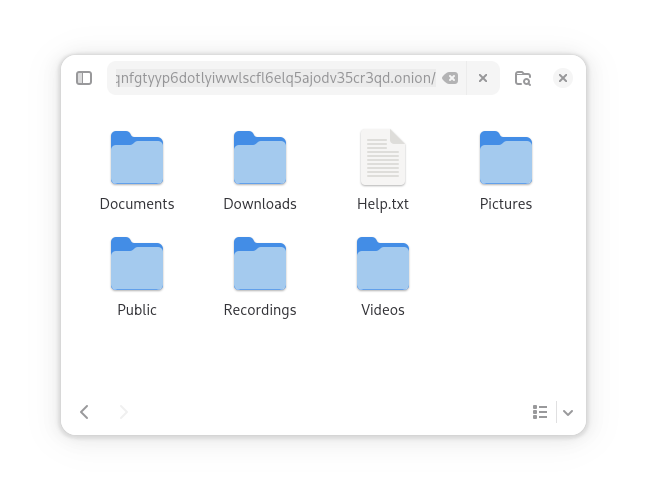
File Manager Integration
Manage files through a familiar interface using any WebDAV client. Access your data remotely using built-in Tor onion services.

Accept Files Anonymously
Tor hidden service integration for receiving files anonymously and securely into your encrypted virtual filesystem.
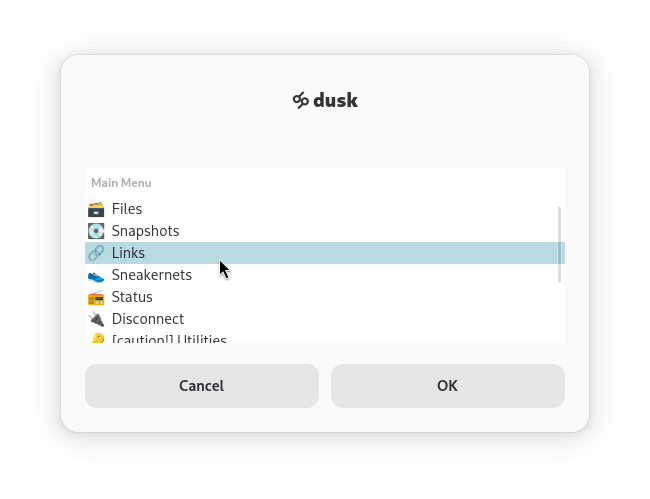
Settings Application
Simple desktop menu to manage settings, link other devices, and use a graphical wizard for creating USB sneakernets completely offline.
Is 🝰 dusk for you?

If you are an activist, journalist, or researcher that handles sensitive files, dusk is designed to keep you and your friends safe.
Your files are encrypted, shredded into uniform blocks, encoded with recovery information, and spread across a network of Tor hidden services. Files can only be retraced with an encrypted pointer that you keep and secret key that only you can unlock. If you work in a high-risk environment under threat of physical device seizure, dusk can help protect your data and shield your personal networks.
Offline Mode
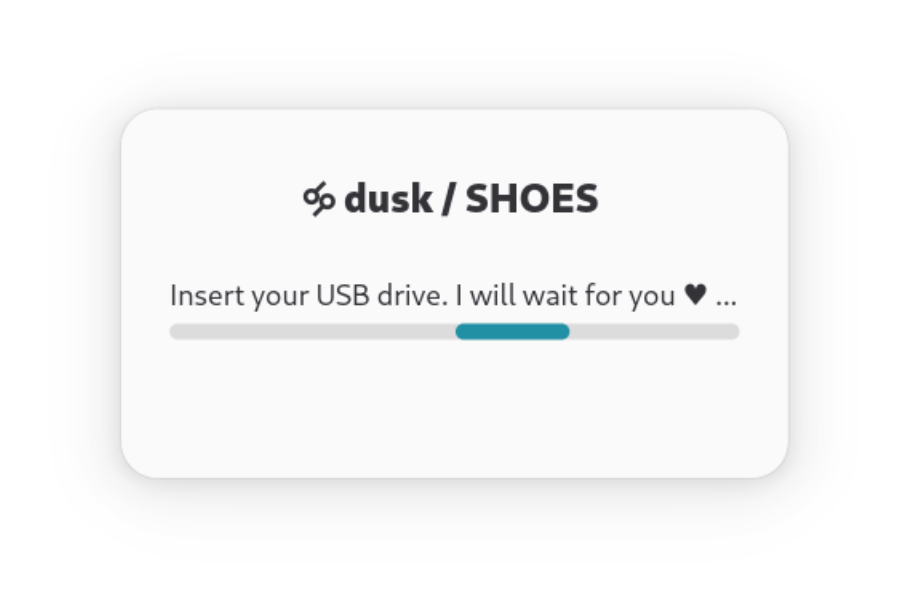
Works without a network or internet connection. Create USB sneakernets with your friends - make files only unlockable if a critical mass is present.
If someone is compromised, data is still safe from adversaries and recoverable by uncompromised members.
anti-copyright, 2024 tactical chihuahua | licensed agpl 3
source code | contribute | bug reports
🝰 dusk is proudly antifascist